
Board of Innovation is a global innovation firm imagining tomorrow’s products, services, and businesses – and creating them today. The company joins forces with the world’s most ambitious businesses to make what life needs next.

The challenge
Trust over control within client confidentiality
The company culture at Board of Innovation is based on trust and employee enablement. These are critical elements for a creative industry. To succeed, the company is remote-first, and collaboration with freelancers and consultants of different backgrounds supplements full-time employees to generate new-of-the-kind products and services.
“Board of Innovation team is diverse as we have around 100 people of about 30 different nationalities in 60 places varying in cities, countries, and continents.”
Yet, with a dynamic network of company innovators, consultants who move to client facilities, and third-party partners, IT managers face many challenges maintaining high levels of security that don’t interfere with team workflow.
“Business with client companies makes data security and confidentiality imperative, balancing it with the IT Manager’s responsibility to ensure the team works efficiently and effectively.”
Board of Innovation works with high-profile companies and industry leaders. High traffic of changing projects, collaborators, and partners also requires precise supervision to mitigate the risks.
Since employees are unrestricted with their choices of how they want to work, self-awareness of the entire organization must be on board to achieve security goals. But how does one define the proper data protection standards and make security implicit yet not dominant? It’s a tough and subtle challenge for the IT manager to tackle.
The solution
Depicting minimums of must-security
With evaluation of team setup, work environments, and the need for flexibility, a VPN solution was the most straightforward tool for Board of Innovation. It enables many different security protocols defined in the company. One of the policies is establishing a safe connection to the company network — this is where NordLayer comes into play.
A newly assigned IT manager started by reviewing the then-current cybersecurity strategy applied in the organization. Deployed by the previous responsible manager, Board of Innovation already had an ongoing NordLayer subscription. Yet, it needed a strategy that fits company culture to its benefit.
“I’ve started by revisiting and improving the existing cybersecurity setup. NordLayer was there but not utilized to its fullest potential.”
So what needed to be added to create a sound cybersecurity strategy that works?
The company has a secure network access solution in place. VPN is a mandatory factor of encrypted connection, and every organization member has to familiarize themselves and agree to data protection policies.
“Whether our collaborators and employees use personal or corporate devices for the job, they must acknowledge internal IT security policies to follow.”
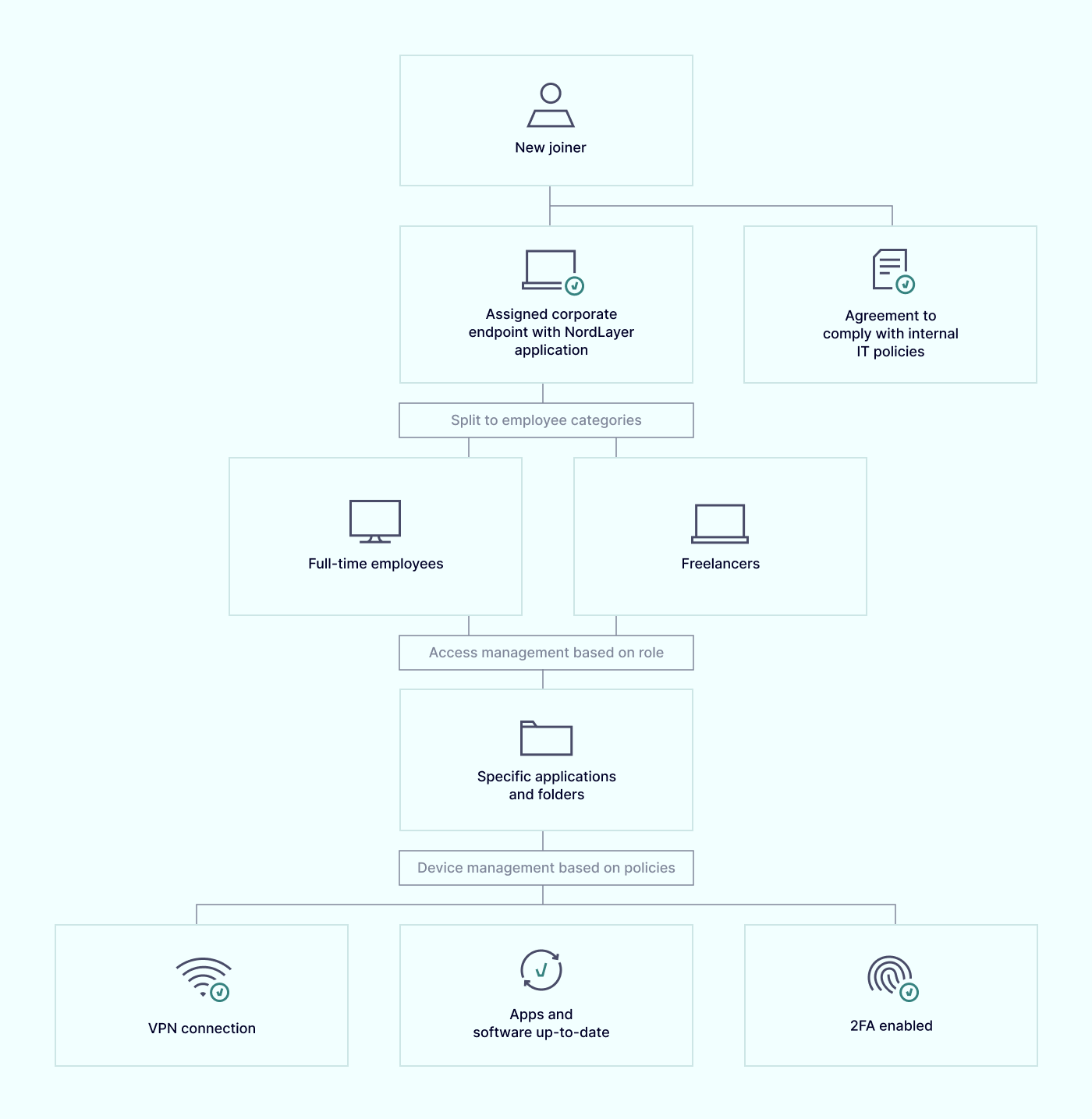
Board of Innovation follows a streamlined approach to managing its workforce — company policies define access levels to internal data. To put policies into force, corporate devices became a connecting point for every user with access to company resources.
“Mandatory apps like NordLayer and tools for password management, specific internet navigation, and work organization are pre-installed by default. That’s how we enforce security via device management on corporate devices.”
Having the tools that fulfill internal and client data security requirements relieves the security manager from dependency on employees. And having those corporate devices set up and readily distributed to the hands of the workforce is half the job done.
Users have to launch VPN once connecting to untrusted networks wherever and whenever they work, and the admin can supervise the whole process if the rules are followed.
Why choose NordLayer
Creative freedom and trust are the fou
ndation of the Board of Innovation culture. Thus, any tools and solutions used to keep up with the security requirements must be convenient and simple, enabling and not disrupting the workers.
The organization decided to keep the NordLayer solution due to its user-friendliness. Moreover, the well-known service provider has to sustain being a reputable vendor of a safe and efficient solution.
Role and endpoint management leaves more space for protecting digital company assets by enforcing authenticated user identities. More granular network access segmentation enables careful supervision over the organization members.
How NordLayer enables data security on different network layers
The outcome
Streamlined consistency aligned with internal policies
Now, Board of Innovation has all workforce onboarded to the NordLayer solution. The solution present in every corporate device and combined with two-factor authentication makes it easier for the IT manager to ensure policies are up and running.
“We distribute NordLayer licenses to all organization members and contributors as a basic rule in our company. We aim to reinforce security policies in as many places as possible.”
The remote network access solution enables the organization to collaborate with various clients, partners, and freelancers. Managing access to internal resources and project information creates barriers to stopping data leaks and breaches. And importantly, security policies don’t overcome and interrupt innovators’ creativity and workflow.
“Using NordLayer is so easy — simply open the user interface, choose a gateway, get connected, and here you go.”
All that is left for the IT manager is to distribute access and privileges to internal resources according to the company policies and check that everyone is on board with the process.
Pro cybersecurity tips
Sharing best practices is what helps businesses of any industry innovate in their own way of security. Creating a strategy for protecting the company network and securing information of different levels can be based on the most unconventional and unexpected advice. Thus, this time just like every time, we asked Mehdi Lahmamsi Pinel, the Global Operations & IT Manager at Board of Innovation, to share his professional insights on business cybersecurity:

NordLayer solution secures and enables every way of working, even if you want to prioritize trust and flexibility. The application, running in the background, simply does its job encrypting connections and segmenting the teams wherever the employees are. They can combine organization-provided devices with personal endpoints securely enabling BYOD policy within the company and IT managers can attend to their work stress-free. Sounds good? Reach out to learn more about NordLayer possibilities.



